In a span of 24hrs I just got one of the biggest scares in my digital existence…
ADL Interactive Got Hacked!!!
Short recap: I went to bed last night after I finished touching up some posts and publishing a new post. Still trying to figure out what site builder I want to use. One that doesn’t override my theme’s posts types and other features but still gives me responsive, manageable columns and cool widgets to use on page. But that’s beside the point. After I had logged off I crashed.
Night time … sleep
After finishing up my Friday work I jumped right back into my account to continue to put a dent in my Pending list and create graphics for my drafts. Lo and behold when I refreshed my homepage I got a redirect that prompted me to accept a desktop notification. I chose Never, as usual, but then it refreshed. Refreshed the browser’s URL by appending a 1 subdomain and prompted me again. I declined… again! Refresh. Amend. Repeat. I was like WTF??!!
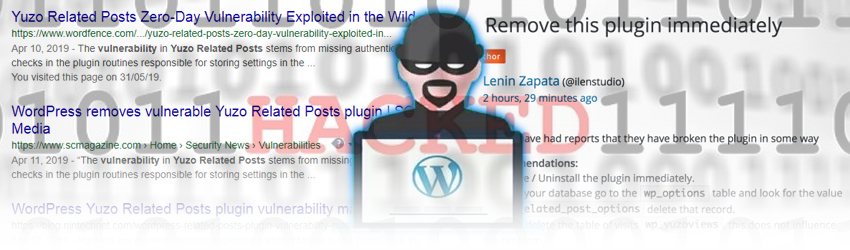
I instantly jumped into my account, looked through my Wordfence settings and performed a scan. Everything was gravy. I’ve seen this behaviour before, so the first thing I though was injection. I instantly went to [simple_tooltip content=’If you’ve NEVER run a site check and you own a WP site, I highly recommend you do so right now. And do it once weekly. It’s like that digital apple that could save you from painful site surgery later.’]Sucuri Site Check[/simple_tooltip] website and ran a test. Aaaaannnnnd I was right. Sucuri output the injection code and I jumped into phpMyAdmin. Now, not everyone has access to their hosting cPanel or know how to dig for these things, but if you do it’s best to stay educated on how to help yourself. The wonders and hindrances of self-hosted WP sites. I would recommend finding someone you know to help with things like this because paying a service could cost you a pretty penny.
Get outta here you
I found the string with a full database search, hiding in the wp_options table. I open the table and there it is bright as day. YUZO. I removed the text that Sucuri had identified and saved, then promptly deactivated the plugin and deleted it completely from my install. I took a screenshot of my database results showing the affected, or in this case, infected plug to send to them. As I jump in the forum, bam! Yuzo this, and exploit that. It was old news. Well, time to read what this is all about. After a little digging, Google sleuth style, I found the history on this plugin development and how this whole issue had been a thing since April. I’m such a fool. I don’t keep up with the WP community or the Security Forums that are out there. So much information to sift through it can get overwhelming. For those interested in the developer’s view on the situation, read what Lenin has to say.

A cautionary tale
I feel as though I dodged a bullet, and for two reasons:
- If I had not been actively working on my game blog the last 2 days I would have not picked this up. All the visitors I was getting would have just locked down the tab and never come back again.
- This could have been around for much longer (I do find myself taking hiatus more often than not), and there may have been more than just a redirect script injected.
Brush up on your php skills, get access to your cPanel and keep an eye on the forums. There’s always a storm brewing. Don’t get caught in the rain.

